You’ve embraced Local Control, ensuring your Thinking Home processes data within your own walls for unmatched privacy and reliability. This is a formidable foundation! However, as powerful as local control is, it’s not a magic shield against all threats. A locally controlled hub operating on an insecure network is like a locked safe in a house with no doors—the contents are secure, but the container is exposed.
To truly fortify your Thinking Home, you must adopt the core principle of professional cybersecurity: layered security, also known as defense in depth. This strategy acknowledges that no single defense is impenetrable. Instead, it builds multiple, overlapping layers of protection. Think of your home network as a medieval castle:
- The router’s firewall is the moat and outer wall, the first line of defense against the outside world.
- Isolating devices with Virtual LANs (VLANs) creates inner walls and segregated courtyards, containing threats if the outer wall is breached.
- Strong Passwords and Two-Factor Authentication are the locks on the keep itself, protecting the brain of the operation.
- Secure Remote Access is the secret, guarded tunnel, providing a safe way in and out without compromising the main gate.
This layered approach is an act of Intelligent Sovereignty, making your home a true digital sanctuary—private, resilient, and secure.
Layer 1: The Network Foundation – Securing the Gateway
Your router is the gateway connecting your private home network to the public internet, making it the primary target for external attacks. A 2025 security report revealed that routers are the most vulnerable device category, accounting for a staggering 75% of all infected IoT devices. Securing this gateway is the absolute, non-negotiable first step:
- Change Default Passwords: Default administrative passwords are public knowledge and the first target for automated attack scripts.
- Strong Wi-Fi Encryption: Use WPA3 (or WPA2-AES) for robust protection against modern brute-force attacks.
- Firmware Updates: Keep your router’s firmware constantly updated to patch newly discovered security vulnerabilities.
- Disable WPS, UPnP, and Remote Management: These features, while convenient, have documented vulnerabilities that can allow attackers to gain access or create hidden backdoors into your network.
- Use a Guest Network: For a simple layer of segmentation, place visitors and new, untrusted IoT devices on an isolated Guest or IoT Network. For power users, implementing VLANs creates a much stronger IoT Ghetto.
Layer 2: The Hub & Software – Hardening the Brain
Once your network foundation is secure, the next layer of defense focuses on your smart home hub itself:
- Strong, Unique Passwords: Every user account on your hub (e.g., Home Assistant) needs a strong, unique password.
- Two-Factor Authentication (2FA): This is a mandatory security measure. Even if your password is stolen, 2FA (using a code from your phone) prevents unauthorized login.
- Update Discipline: Regularly check for and install updates for your hub’s core software, operating system, and all add-ons. Neglecting updates leaves your system exposed to known exploits.
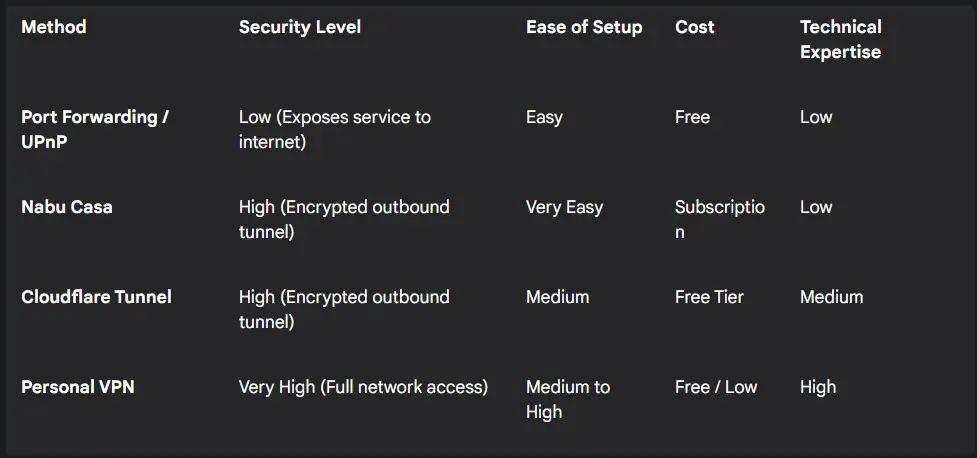
Layer 3: Secure Remote Access – The Secret Tunnel
The ability to control your home while away is vital, but creating this remote link is one of the most common ways users inadvertently expose their system.
- Avoid Port Forwarding and UPnP: Manually opening ports on your router or using UPnP creates unguarded holes in your firewall, inviting attacks from the internet.
- Embrace Secure Tunnels: The safest methods for remote access use secure, outbound-only connections. The official Home Assistant Cloud by Nabu Casa provides a simple, encrypted tunnel. For self-hosted alternatives, consider Cloudflare Tunnels or Personal VPNs like WireGuard or Tailscale.
By building these layers of defense, you ensure that your Thinking Home is not just intelligent, but truly a digital sanctuary, providing unparalleled privacy and security.
For a comprehensive guide to implementing a layered security strategy, including detailed firewall rules and remote access options, consult Appendix I: Fortifying Your Thinking Home: A Layered Security Strategy in The Thinking Home.